Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
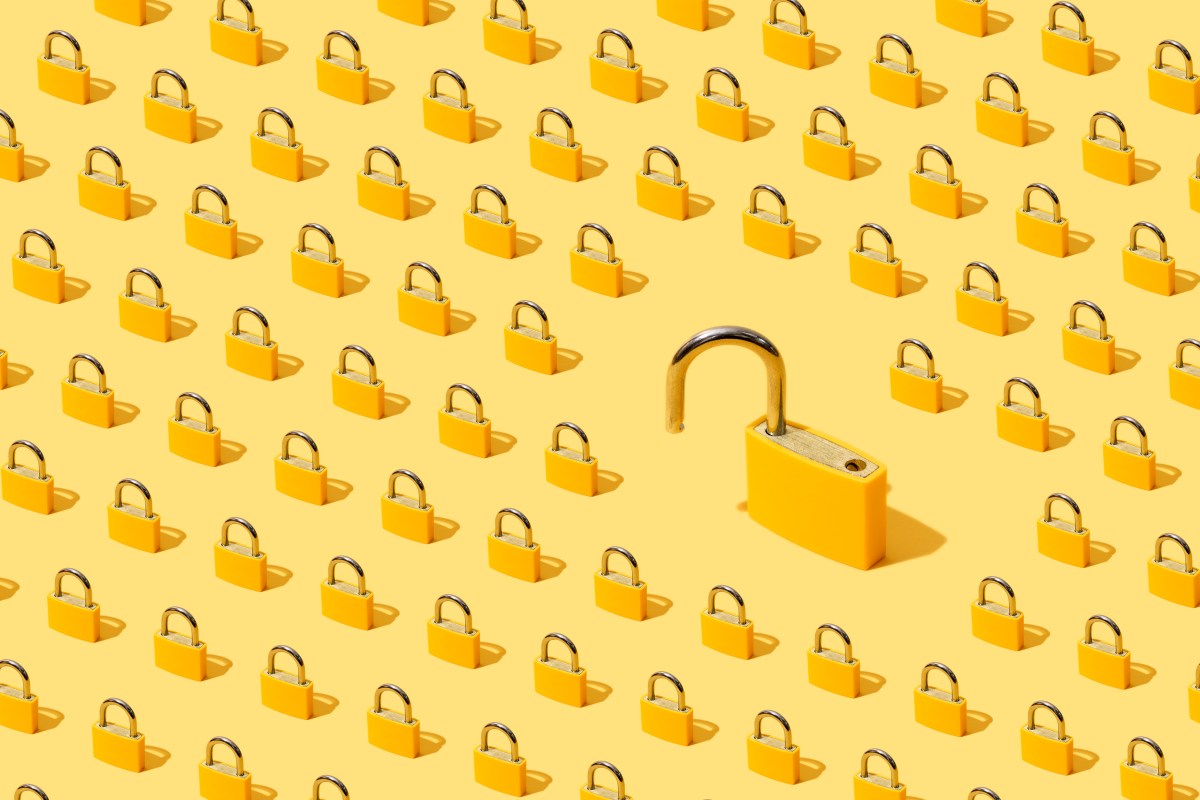
Talking about Backdors that have work happens again The reports are out that the UK government requires to force an apple to open Iclloumot Dodd-Tod-Closed (E2EE) Shipment of a storage device. Adults have been reported to lean apple to make “Backdor” in a work that will be able to get the data clearly.
UK has had a lighter energy to reduce the use of the users’ to use a strong hard work from the passage of the 2016 changes of the state of State. According to the statement of Washington PostThe UK officials have used the underlying power
Apple’s Apple’s Apple Service design is made in a way that even the Tech’s giant will not have the keys The end-end (Aeee) – To allow an apple to promote that contains “zero’s knowledge” of those who use.
A back door It’s the words that are provided to explain a secret of hiding, or otherwise, safety methods to help the third party. In ICloud case, the order allows the UK one UK
When the UK Government rejects to verify or reject information provided to the information provided under IP, security experts warns that such a system May have more in the world If the iphone designer is forced to lift security supplies offer to all users, including those outside the United Kingdom.
Once at the applicant is available, there is some accidents that can be used with other types of agents, say the contrary to theft, or to make a difficult data, or even to give a ranshares.
This can explain why the famous machine used for a state of the state to get e2ee with the souvenir of Backroor; to ask a Maintaining a Heart stay deliberately In addition to the code makes products to sell.
To apply the example: When there are pickets for physical doors – indoors, walls, or as – is not confirmed to be the owner of the company.
The opening available, makes – someone else can find a key, for example, or to force their way to break the door.
The bottom line: There is no choice a door that only lets someone pass a person pass. If one may enter, it is clear that someone can also use the door.
The same is one login point applies additional use of the software (or, actually, specified).
The idea of Nobus (“No one but us”) returns floating with security security. This unique color is only to give their skills to use something more than all others – safely able to reach their resources.
But in nature, technical skills and the ability to be changed. Testing the skills of other unknown ones are no real science. “Nobus” views on a suspicious views; Any third of the third makes the risk of opening new vectors to get up, like the highest paths of people who want a person to have a legitimate advantage.
Silently, many protectists are telling them noblus as a wrong idea. In short, every chance makes risk; Therefore, pushing backs and disregards a strong security.
However, regardless of clear concern and existing concern, Governments continue to press back. That’s why we’re going to talk about them.
The word “back” refers to the requests to be a cardboard box, not in public – just as the houses don’t match the login. In the Apple’s Apple’s story, a request distracted by IPA – in the way of “skills,” or TCN – cannot be legally revealed by the receiver. The purpose of the law is that any returns are hidden. .
According to the Freedom of Freedom The basis of lightsThe word “Boxid” went to the 1980s, while returns (and “a” diams “) was used to refer to the hidden accounts and / or passwords made for a person. But over the years, the words are used to write several tests to solve, pornography, or distinguishing data safety.
While returns of returns, because of the UK goes after Apple ICloups, it is important to know that data presence At the beginning of the years.
Back, for instance, US National Agency (nsa) that was designed to prepare a word with data message with a cooking hope – with a purpose permitting functionality. A chip of “Clipper,” As perceived, using a form of inspiration escroun – which means the encryption device was made by government agencies to obtain data to access the state of the state required.
The paper attempts to Flog cooking and cooks-in-marked rooms have failed because of not giving birth after the security of the secret security and determination. Although clipper leather is known to help the fire to the test and publish the Encryrapts required to protect update data.
This scatter is a good example they try to use a plan to reach a plan. It is important to note that in the houses don’t have to be a secret all the time. .
Add that, governments often sends wild lies, or avoid other serious crimes.
Returns can have a way to get to the way to win their creatures, yet. For example, Plants in China was behind Feecical Virus the last fall – Seems to get USCOS USPOS and ISPS Due to the 30-year-old laws that were ordered to get the return returns.
Governments also masters foreign foreign exterior and forming the hazards of their citizens and secular security.
There has been a series of China’s Hardwares of China and Apps to be looked with what can be in the home many years. That affect the dangers return to other countries, In addition to UKTo take action to remove or reduce Chinese activities, as used in the tie telecommunications, in recent years. The fear of the back, too, can be strong.